Managing groups using SAML
There are two available options when managing groups with SAML, both of which are described below. These two options can be combined.
Default groups
These are groups that are configured in FotoWeb's SAML settings interface in the site configuration: Default groups and Linked groups.
From the Tools menu (cogwheel icon), go to Site Configuration > Security > Single Sign-on.
By defining at least one default group, all users who log in with SAML will be allowed access and placed in these default FotoWeb groups on import.
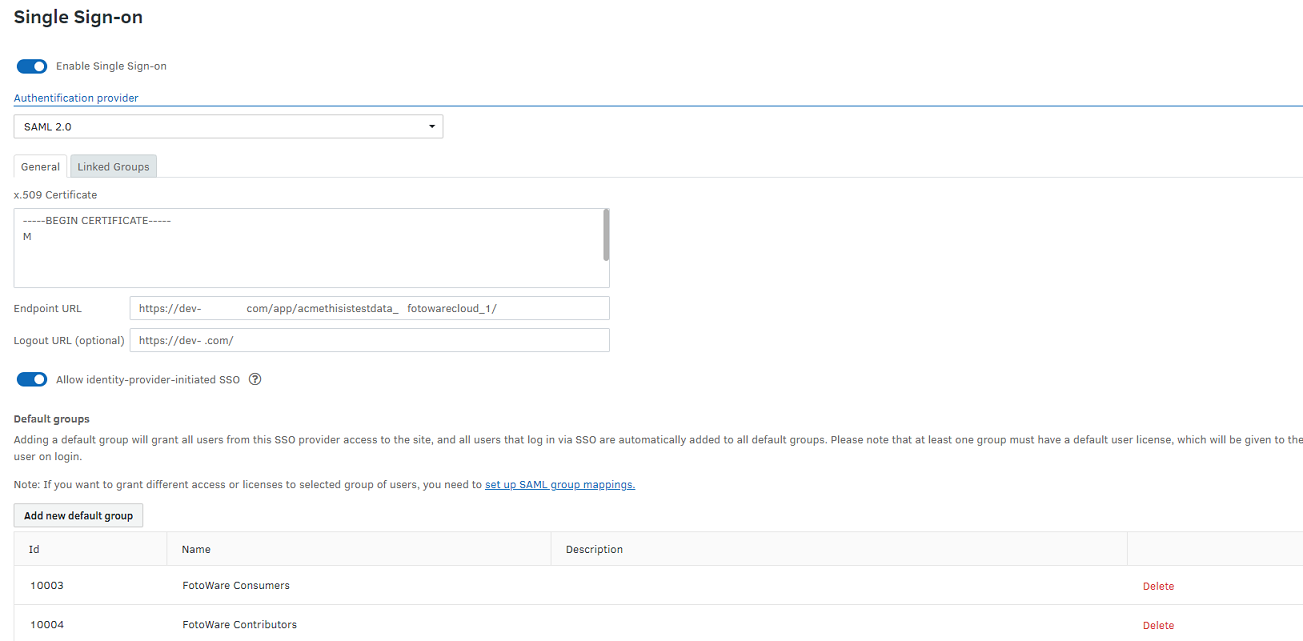
For example, you can create a SAML Users group in FotoWeb and add it as a default group. All users who log in using SAML SSO are then placed in this group and are assigned access to the system accordingly. In the example above, two default groups are defined: FotoWare Consumers and FotoWare Contributors. Users imported via SAML will be placed in these groups and be assigned a license and permissions according to these groups' settings.
Linked Groups
On the Linked Groups tab, you find FotoWeb groups that are linked to groups in the SAML Identity Provider (IdP). When using ADFS, the IdP will be Active Directory.
When a user logs in with SAML SSO, that user will be added to one or more linked groups based on the group information obtained from the IdP.
For example, it's possible to create a group called FW-Editors in FotoWeb and configure it as a linked group (Select Add linked group) so that all members of the Active Directory group AD-Editors are added to the corresponding FW-Editors group in FotoWeb when they log in. This way, groups can be managed in the IdP, synced to FotoWeb, and used for fine-grained access control based on group membership or other attributes set in the IdP.
Configuring a linked group
- Create a group in FotoWeb. For this example, let's name it Photo Editors. Set the group permissions, select the license that should apply to the group, and any parent group that the group should be nested in.
- In the group details, the SAML group name should be the group attribute value that comes from the IdP. In the example below, the value from the IdP is adfs_editors.
- In the Identity Provider, configure an attribute mapping rule for group membership(s) that transfer group names as values of the attribute.
How to perform this step depends on the Identity Provider. For example, in Microsoft ADFS, you can:
- add a claim rule (which is called an attribute mapping in SAML) of type Send group membership as claim,
- select an Active Directory group to be linked to the FotoWeb group,
- set the outgoing claim type (= SAML attribute mapping) to Groups (or whatever SAML Property name is used for the FotoWeb Member of (Group) property) and set the outgoing claim value to same value as the SAML group name for the group in FotoWeb.
This is described below. For additional information from Microsoft, see https://docs.microsoft.com/en-us/win...hip-as-a-claim.
Note: The certificates used for SAML SSO must be renewed before they expire, otherwise users will temporarily lose access to the system. Each customer has the responsibility to avoid this situation. We recommend setting reminders and designating responsibility so that there is always someone available to renew the certificates when necessary.
In the following, ADFS is used to illustrate the attributes that need to be mapped. However, the same can be accomplished by configuring FotoWeb with a SAML interface toward other Identity Providers.
Example: Mapping AD groups to FotoWeb groups in Microsoft ADFS
- In the ADFS manager, right-click the selected trust and select Edit Claim Issuance Policy.
- The Claim Issuance Policy window opens. Add one rule for every group you'd like to link to FotoWeb.
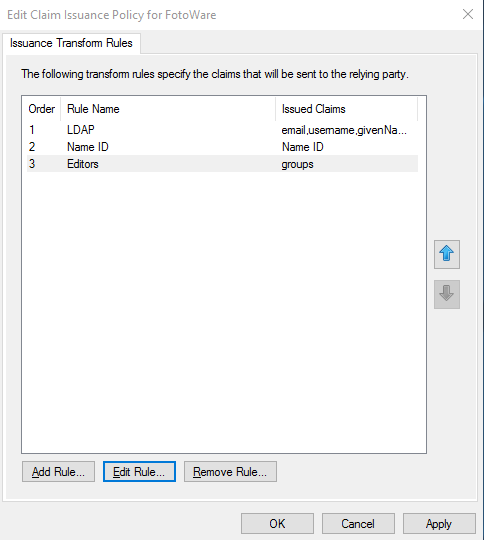
Note: In the example above, Entry 3 in the list is the group claim. You can find information on setting up entries 1 and 2 (LDAP and Name ID mapping) below.
- Select Add Rule to create a new rule.
- From the Claim rule template drop-down list, choose Send Group Membership as a Claim.
- Enter the rule specifics:
Claim rule name is used to identify the rule. Give it a name that allows you to identify it easily later.
Choice of group: Choose the group that should be synced to FotoWeb. Select Browse to select a group in the Identify Provider (AD)
User's group: Do not select a value from the drop-down list; instead, enter the SAML Attribute Name corresponding to the FotoWeb Member of (Groups) property - it's typically called groups unless you've changed the default value. This allows FotoWeb to identify the transferred claim as a group attribute.
Outgoing claim value: Here, enter a unique name that will be used to identify the group when linking it to a group in FotoWeb. It does not have to have the same name as the group; the value must be identical to the SAML group name specified in the FotoWeb group. (adfs_editors was used in the example FotoWeb group above - the example below reflects this.)
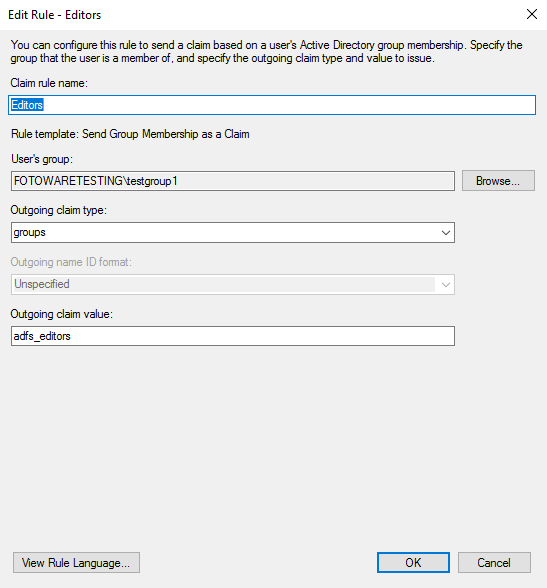
You can also specify multiple groups in the groups attribute separated by commas. For example, a value of group1,group2 will cause the user to be added to the linked groups where the SAML group name is group1 or group2. How to set the attribute like this depends on the Identity Provider. To our knowledge, it is not easily possible in ADFS.
How are groups synchronized?
Upon login, the user will be removed from any linked groups with a SAML group name not listed in the groups attribute. This allows an administrator to revoke a user's access to resources in FotoWeb by, from example, removing the user from a group in Active Directory. In no event is the user removed from any groups with no SAML group name (FotoWeb groups that are not linked groups).
A user can log in to FotoWeb via SAML SSO if and only if the user is added to at least one linked group, or if at least one default group is configured.
This means that if any default groups are configured, then all users that can successfully sign in via SAML SSO have permission to log in to FotoWeb, and if no default groups are configured, then membership of linked groups can be used to control access to FotoWeb in general. Note that most SAML Identity Providers also have configurable access control, so it is possible to configure access control even when using default groups.
Example: How do you assign different user licenses to different user groups?
Based on the information above, here's an example that illustrates how to control the assignment of user licenses (Standard, Plus, Pro) based on group membership in the IdP. Note that the example is based on FotoWeb Feature Release 13 and later - it won't work with earlier versions.
- Create a group AD Pro Users in Active Directory and add all users/groups that should receive a Pro license.
- Create a group FW Pro Users in FotoWeb and set the default license to Pro.
- Set the SAML name of the group to
pro_users. - In ADFS, create a new Send Group Membership as a Claim rule.
- Select the AD group AD Pro Users.
- Set Outgoing claim type (= SAML Attribute name) to
groups(enter the value; do not select from the drop-down list). - Set Outgoing claim value to
pro_users.
Licenses can now be managed in AD by adding/removing users/groups to/from the group AD Pro Users.
The names and identifiers can be varied. The examples above are chosen as placeholders to illustrate which names must match or not.
